Official code hash
| Contract version | Hash |
|---|---|
| V5 R1 | 20834b7b72b112147e1b2fb457b84e74d1a30f04f737d4f62a668e9552d2b72f |
Persistent memory layout
ContractState, compared to previous versions, hasn’t undergone major changes. The main difference is the new is_signature_allowed 1-bit flag, which restricts or allows access through the signature and stored public key. We will describe the importance of this change in later topics.
Authentication process
InnerRequest — let’s first look at how version 5 differs from previous versions in the authentication process. The InternalMsgBody combinator describes two ways to access wallet actions through internal messages. The first method is one we are already familiar with from version 4: authentication as a previously registered extension, the address of which is stored in extensions_dict. The second method is authentication through the stored public key and signature, similar to external requests.
At first, this might seem like an unnecessary feature, but it actually enables requests to be processed through external services (smart contracts) that are not part of your wallet’s extension infrastructure — a key feature of V5. Gasless transactions rely on this functionality.
Note that simply receiving funds is still an option. Practically, any received internal message that doesn’t pass the authentication process will be considered a transfer.
Actions
The first thing that we should notice isInnerRequest, which we have already seen in the authentication process. In contrast to the previous version, both external and internal messages have access to the same functionality, except for changing the signature mode (i.e., the is_signature_allowed flag).
InnerRequest as two lists of actions: the first, OutList, is an optional chain of cell references, each containing a send message request led by the message mode. The second, ActionList, is led by a one-bit flag, has_other_actions, which marks the presence of extended actions, starting from the first cell and continuing as a chain of cell references. We are already familiar with the first two extended actions, action_add_ext and action_delete_ext, followed by the internal address that we want to add or delete from the extensions dictionary. The third, action_set_signature_auth_allowed, restricts or allows authentication through the public key, leaving the only way to interact with the wallet through extensions. This functionality might be extremely important in the case of a lost or compromised private key.
Exit codes
| Exit code | Description |
|---|---|
| 132 | Authentication attempt through signature while it’s disabled |
| 133 | seqno check failed, replay protection occurred |
| 134 | wallet_id does not correspond to the stored one |
| 135 | Ed25519 signature check failed |
| 136 | valid-until check failed |
| 137 | Enforce that send_mode has the +2 bit (ignore errors) set for external messages. |
| 138 | external_signed prefix doesn’t correspond to the received one |
| 139 | Add extension operation was not successful |
| 140 | Remove extension operation was not successful |
| 141 | Unsupported extended message prefix |
| 142 | Tried to disable auth by signature while the extension dictionary is empty |
| 143 | Attempt to set signature to an already set state |
| 144 | Tried to remove the last extension when signature is disabled |
| 145 | Extension has the wrong workchain |
| 146 | Tried to change signature mode through external message |
| 147 | Invalid c5, action_send_msg verification failed |
| 0 | Standard successful execution exit code. |
Get methods
int is_signature_allowed()returns storedis_signature_allowedflag.int seqno()returns current stored seqno.int get_wallet_id()returns current wallet ID.int get_public_key()returns current stored public key.cell get_extensions()returns extensions dictionary.
Preparing for gasless transactions
Starting with v5, the wallet smart contract supports owner-signed internal messages (internal_signed), which enables gasless transactions—for example, paying network fees in USDt when transferring USDt. The common scheme looks like this:
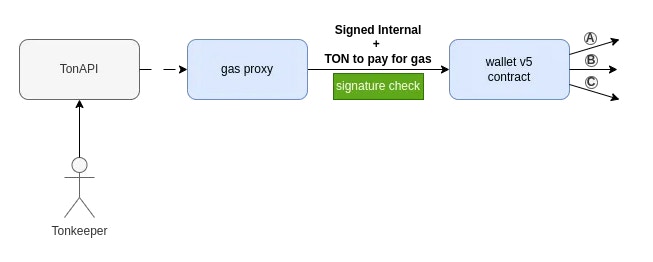
Flow
- When sending USDt, the user signs one message containing two outgoing USDt transfers:
- USDt transfer to the recipient’s address.
- Transfer of a small amount of USDt in favor of the service.
- This signed message is sent off-chain by HTTPS to the service backend. The service backend sends it to the TON Blockchain, paying Toncoin for network fees.